Following on from Remote Desktop Services Manager and Remote Desktop Session Host Configuration missing from Server 2012
I need to create a secure connection to a terminal server, only allowing some users external access, while other users only have external access.
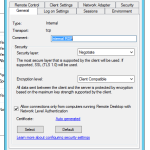
Once Remote Desktop Session Host is open. Find the current connector. Rename it to something smart like Internal Connector.
This makes it easier to know what your working with.
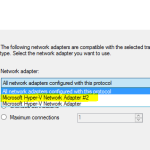
Then select the Network Adapter tab, and change the Network Adapter from “All Network Adapters configured with this protocol” to Microsoft Hyper-V Network Adapter or what ever your NIC is called.
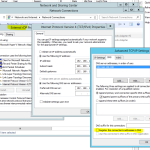
Head to Network and Sharing Center > Network Connections and locate your NIC here. Rename this to the same name as you called the connector.
From here, we need to shut down the server and add in an additional NIC. Hyper-V makes this easy. It just needs to be another normal NIC.
Once the server is back online, Head back to Network and Sharing Center > Network Connections then locate the new NIC you created/installed. Rename it to external, and give it a fixed IP address (i assume that you already had the internal NIC with a static address)
Click on Advanced > DNS Then untick Registers this connection’s address in DNS. We dont want internal client knowing about this NIC as it will cause problems.
Now head back to Remote Desktop Session Host and Create New Connector. Give it a name, external with the comment the same. Select the network adapter, chances are this will be Number two
Then hit finish.
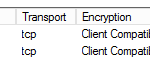
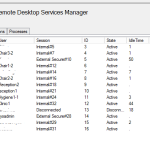
you should now have two connectors
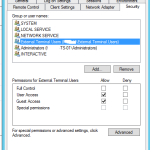
Select your external connector > properties > then click on Security
Add in an AD Group you have created for the external users. In my case, External.Terminal.Users
for the internal connector, for this client, i have domain users as the internal users, as they only use terminal servers.
Now depending on how your server feels, once you reboot, you might not be able to connect to both IP addresses. Some times it will have a problem starting both connectors. If this happens to you, then its an easy fix.
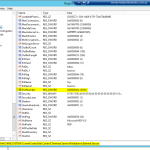
Open Regedit
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\External Secure
Then locate PortNumber Change this to another port. In my case 3390
Reboot the server, then test on both IPs
192.168.1.110 (This is the internal NIC)
192.168.1.111:3390 (This is the IP address of the second NIC and port 3390)
If all goes to plan, then you should be able to see users connecting in on both connectors.
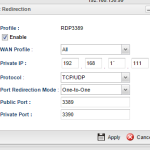
From there, all that’s needed is to publish this into your router.
Here is a screen shot of mine. Its running port translation. From the public address on port 3389 its sending off to the internal server on port 3390. This means that external clients dont need to know anything more than the normal address to connect in, they dont have to worry about a port number on the end.
Now you can have crap password on the generic internal accounts and not have the security risk associated with them 🙂
« Remote Desktop Services Manager and Remote Desktop Session Host Configuration missing from Server 2012 Script to create Remote Mailboxes Office 365 »